Procurement moves quickly when risk reviews are fast and consistent. The problem is that manual vendor questionnaires, scattered evidence, email approvals, and last minute renewals slow everything down. In this playbook I will show you how vendor risk management automation turns intake through renewal into a single auditable workflow. You will see how vendor security questionnaire automation, automated approvals, continuous vendor monitoring, and contract renewal automation can shorten cycle time without lowering your risk bar.
At Evening Sky we build custom automation and workflows for growth minded teams that want speed and control at the same time. This guide shares what we have learned building practical systems, links to standards like SIG and CAIQ for repeatable assessments, and shows where modern tools help. Throughout, I include references to authoritative sources so your program stays aligned with industry guidance.
Why manual reviews slow purchasing
Most teams start vendor reviews with spreadsheets, shared drives, and long email threads. That works for a handful of vendors, then it cracks. Intake forms are incomplete, the same questions are asked in five different ways, and approvers are left waiting for missing details. Each handoff adds days and no one has a single view of risk. Procurement stalls and the business gets frustrated.
Automation removes duplicate work and shortens handoffs. Procurement leaders consistently list vendor onboarding, approval routing, and document management among the top processes to automate because cycle time falls and policy adherence improves. See GEPs perspective on top procurement processes to automate for a solid overview here.
The goal is not to rubber stamp vendors. The goal is to apply the right level of review every time, prove it with an audit trail, and keep watching after go live. Continuous monitoring reduces reliance on point in time assessments and surfaces vendor issues as they appear, as explained by Bitsight here.
The automated lifecycle
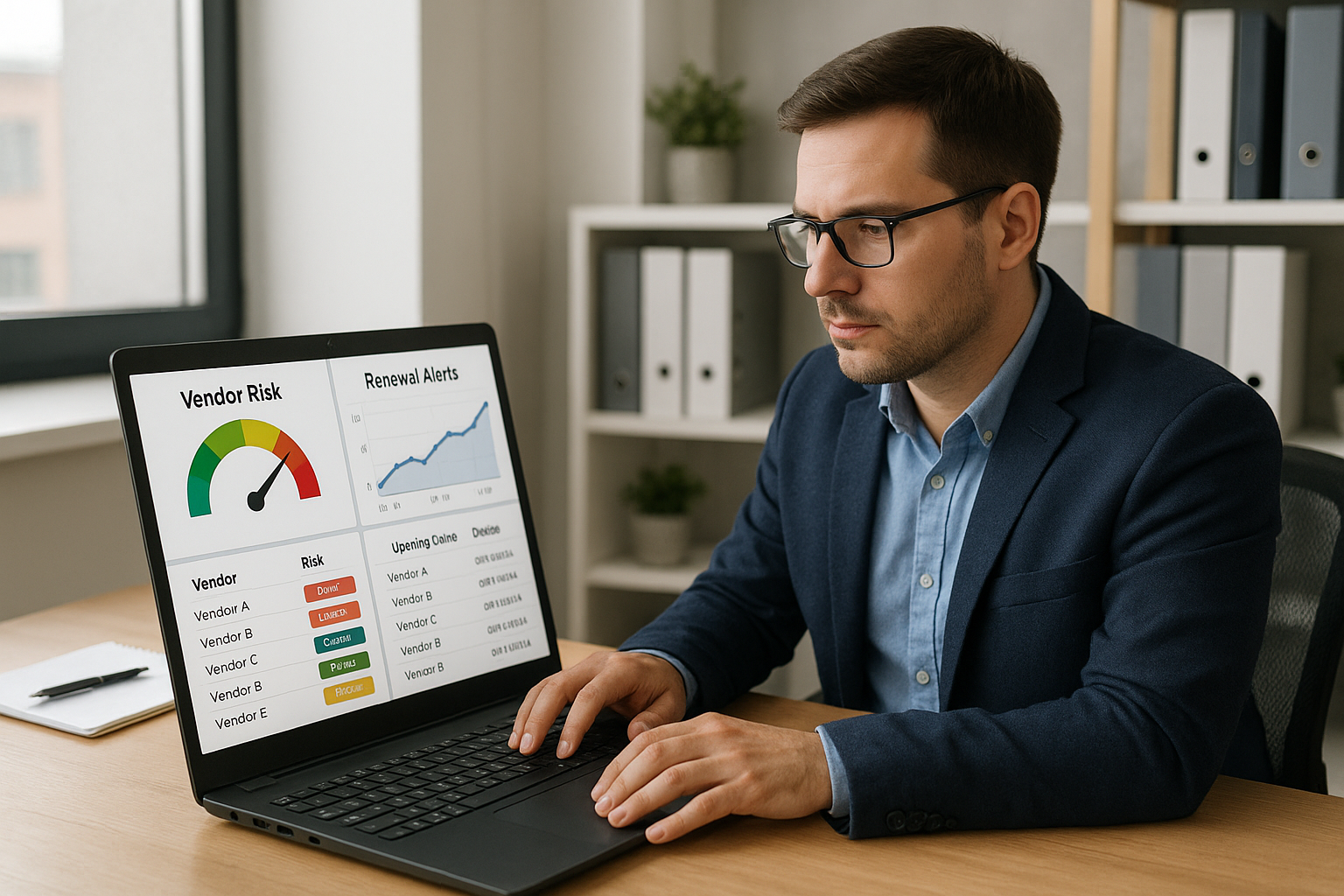
Think of vendor risk as a closed loop. Intake, assessment, approvals and data access, continuous monitoring, and renewals with offboarding. Each stage can be automated without losing judgment or context.
Intake and smart tiering
Start with a single intake form that captures business owner, use case, data types, system boundaries, hosting model, regulatory drivers, and target go live date. Route intake to the right workflow based on tiering rules. For example, a vendor that stores customer personal data will follow a deeper track than a marketing tool with no data exchange. Workday shares a practical guide to onboarding vendors with a focus on clean data capture and clear responsibilities here.
Tiering rules should reflect risk appetite and NIST supply chain guidance. NIST SP 800 161 recommends a lifecycle approach and risk based tiering for third party risk management. You can reference the publication here.
Assessment with standards
Standardized questionnaires make assessments repeatable and automatable. The Shared Assessments SIG has Lite, Core, and Detail versions so you can match depth to risk. Using SIG plus an evidence library lets you map vendor answers to frameworks consistently. Read about the SIG structure here.
For cloud providers, the Cloud Security Alliance CAIQ and the Cloud Controls Matrix bring clarity to control expectations. The CAIQ is a common option for cloud vendors and CAIQ lite variants enable faster cycles for low risk use cases. Review CAIQ details here.
Vendor security questionnaire automation
Even with standards, questionnaires take time. Modern platforms use AI and knowledge bases to pre answer questions from your own policy library and past responses. OneTrust launched questionnaire response automation that can answer security and privacy questionnaires automatically using artificial intelligence, with human review for high risk items. See the announcement here.
Whistic takes a similar route with AI assisted responses and trust catalogs that let buyers review standardized profiles. You can read about the Whistic platform here. Whether you use a product or build a lightweight internal answer library, the pattern is the same. Normalize your approved answers, link them to evidence, and route exceptions to a human.
If you want a quick proof of value, we can automate vendor security questionnaires with our automated task and approval workflows approach and plug it into your intake form.
Approvals and data access
Once a questionnaire is complete, route findings to the right approvers. Automated approval routing and policy based gates reduce manual handoffs and keep everyone honest about who signs off and when. This is where a simple rules engine shines. If a vendor is rated low risk, auto approval with monitoring can be sufficient. If the vendor handles customer personal data or connects to production, require security lead review, legal review, and executive approval. This pattern shortens cycle time while protecting the business, as procurement automation resources like GEP explain here.
Extend approvals into access provisioning. When a vendor account is approved, create it with the right roles, set review dates, and record ownership. When the contract ends or a business owner changes, revoke accounts automatically. Our automated task and approval workflows article shows how these gates and reminders work across teams.
Continuous monitoring
Point in time reviews miss what happens later. Continuous vendor monitoring provides external posture scores, breach alerts, and vulnerability feeds so you can react when risk increases. Bitsight describes how continuous monitoring reduces reliance on point in time assessments and surfaces issues as they appear. Review their guidance here and the related explainer here.
If a vendors score drops or a new vulnerability affects them, your workflow should open a ticket, notify the business owner, and request an action plan. This keeps the loop active between annual reviews.
Renewals and offboarding
Renewals are where many programs lose time and control. Contract lifecycle management systems track dates, send reminders, and attach approvals to contract changes. Automated renewal tracking prevents missed renewals and provides an audit trail for compliance. ContractWorks gives a clear description of this benefit here.
Link renewal gates to a right sized reassessment. Low risk vendors can be renewed after a short update and a look at monitoring results. High risk vendors may require a fresh SIG Core or updated CAIQ. For offboarding, trigger a zero touch checklist that removes access, collects devices if applicable, and archives evidence. Our automated task and approval workflows example covers these routed tasks in practice.
Playbook and sample recipes
Use these recipes to launch or upgrade your vendor risk management automation. Each recipe combines the standards above with simple decision logic.
Recipe A: Low risk vendor
Use this for marketing tools, analytics with aggregate data, or services with no access to customer personal data. Intake routes to a SIG Lite or CAIQ Lite style questionnaire. Ask for a current SOC report or equivalent if available, plus a link to the vendor security page. Your workflow checks that evidence is present, that the questionnaire is complete, and that continuous vendor monitoring is active through a provider like Bitsight or UpGuard. If all checks pass, auto approve and provision access with a standard role and an expiration date. Schedule a renewal review aligned to the contract end date and lean on monitoring for interim changes.
Standardized questionnaires such as the Shared Assessments SIG and the Cloud Security Alliance CAIQ allow repeatable, automatable assessments and simplify mapping to frameworks. See SIG here and CAIQ here.
Recipe B: High risk vendor
Use this for vendors that store or process customer personal data, access production, or are involved in regulated activities. Intake flags the vendor as high risk and triggers a SIG Core questionnaire with evidence requests for encryption, access control, incident response, business continuity, and data residency. Map answers to your controls and record gaps with owners and deadlines. Conditional access rules apply at approval time. For example, provision read only access until data processing terms are executed and one compensating control is implemented.
NIST SP 800 161 encourages a lifecycle approach and risk based tiering. Include continuous monitoring with higher sensitivity. If the monitoring score drops below a threshold or a relevant vulnerability is reported, escalate to your security lead and vendor owner for action. Reference NIST C SCRM guidance here.
Recipe C: Responding to customer questionnaires
Most teams spend many hours each quarter answering incoming customer questionnaires. Build an internal knowledge base of approved responses tied to policy pages, architecture diagrams, and audit reports. Feed that library into a response automation tool or a custom workflow that suggests answers for reviewer approval. AI powered response automation can answer recurring customer and vendor questionnaires by drawing on a knowledge base of policies and past responses, while still keeping a human in the loop for high risk items. See OneTrusts announcement here and the Whistic platform here.
We can help you Automate vendor security questionnaires by building the knowledge base, setting up answer mapping to SIG and CAIQ question groups, and adding routed approval. See how our automated task and approval workflows bring this to life.
See a live demo. We will map intake to renewal and show where you can save days.
KPIs and dashboards that matter
Track a short list of metrics that reflect speed and control. Time to onboard from intake to approved. Share the average, median, and an outlier view to highlight stuck steps. Percentage auto approved within policy by tier. Average days to contract signature and to first access granted. Renewal notice compliance with reminders sent and completed. Distribution of vendor risk scores based on monitoring to see overall exposure and trend. Procurement automation resources like GEP affirm that cycle time and policy adherence are the right signals to watch here, and Bitsight explains how to use continuous monitoring insights in a program here.
Dashboards should let you click from metric to underlying records. If time to onboard creeps up, check which approval step is the bottleneck. If renewal reminders are ignored, confirm whether owners are still valid and whether dates are accurate in the CLM.
Tools and integrations
You can mix off the shelf tools with custom workflow. The right blend depends on your size, volume, and the systems you already run. Below is a compact view of categories and examples.
| Category | Examples | What it automates | Notes |
|---|---|---|---|
| Questionnaire automation | Whistic, OneTrust | AI suggested answers, evidence reuse, trust profiles | Great for vendor or customer questionnaires with repeat content |
| Continuous monitoring | Bitsight, UpGuard | External posture scores, breach alerts, findings workflows | Use alerts to trigger reassessment and owner notifications |
| CLM and renewals | ContractWorks, Conga, Pactly | Contract drafts, e signature, renewal tracking | Connect renewal dates to reassessment workflows and offboarding tasks |
| Workflow engine | Evening Sky custom automation and workflows | Intake, tiering, approvals, provisioning, reminders | Tailored to your data model, policies, and integrations |
| Identity and access | Okta, Azure AD | Account creation, roles, recertification | Drive account changes from risk approvals and renewals |
Compliance and governance
Compliance is not a separate track from automation. It is a property of the workflow and the evidence you store. Use SIG and CAIQ for structured questions and evidence references, which lets you map to frameworks without manual copying. Standardized questionnaires and an evidence library let you automate mapping of vendor answers to compliance frameworks, as Shared Assessments explains here and as CSA documents through CAIQ here.
Adopt NIST C SCRM practices for a lifecycle view. Define tiering criteria, define who approves at each tier, and document escalation paths. Store everything in one place. Questionnaire answers, evidence items, exceptions, approvals, and renewal decisions should all be searchable and exportable for audits. The NIST publication provides a strong foundation for governance here.
Finally, tie continuous vendor monitoring into your governance. Continuous monitoring should be used alongside periodic assessments to capture risks that appear after onboarding, as Bitsight describes here. When monitoring flags an issue, your workflow should generate a risk record, assign an owner, and set due dates for remediation. That is how automation provides both speed and control.
How we build the workflow
Every company has a different mix of tools, policies, and people. That is why we build to fit your environment. The core pattern stays consistent. A single intake with smart tiering sends each vendor down the right track. Questionnaire tasks are created with SIG or CAIQ templates and linked evidence requirements. AI suggested answers speed completion and reduce copy paste work. Approvals follow rules by tier and data type. Identity and CLM systems receive the outcome, then provisioning and renewal reminders happen on time. Continuous monitoring watches for changes between reviews and feeds alerts back into the same queue.
We often start with a two to four week proof of value. We map your current steps and handoffs, then assemble a clickable workflow that shows the path from intake to renewal. The goal is to reduce manual steps quickly and prove the time savings with your own vendors. Our automated task and approval workflows example shows the kind of routing, gating, and reminders we deliver. If you want to see more approaches like this, browse our automation playbooks and guides.
Content and evidence that speed reviews
The fastest programs keep a living evidence library. Think policy PDFs, diagrams, SOC reports, data flow docs, penetration test summaries, and a single page security profile for the company. When a vendor questionnaire asks for encryption at rest, you link the policy and the relevant section of your architecture doc. When a customer asks about incident response, your knowledge base surfaces the approved language instantly. This is the same content you use to fuel vendor security questionnaire automation with Whistic or OneTrust or with your own custom data store.
Set review cadences for each evidence type. Policies might be annual, architecture quarterly, and SOC reports when issued by your auditor. Tag each item with scope and version. The more consistent your library, the faster your team can answer and the easier it is to satisfy audits.
Data access and least privilege in practice
Vendor risk reviews are not just about questionnaires. They are about who gets access to what and for how long. Incorporate least privilege decisions into approval steps. For example, during the approval for a ticketing integration, the workflow presents role choices with clear descriptions and default expiration. If a sensitive role is selected, the workflow asks for a justification and adds a second approver.
Tie expirations to renewals. When a contract enters renewal review, the system pauses access for high risk roles pending approval. When a vendor is terminated, offboarding tasks remove accounts, rotate shared credentials if they were used, and update contact lists. This side of the workflow protects production while keeping the paper trail tight.
Common pitfalls and how to avoid them
Two things commonly slow teams after they start with automation. First, overbuilt questionnaires for low risk vendors. Solve it with tiering rules and SIG Lite or CAIQ Lite for quick cases. Second, fragmented ownership. Assign a clear business owner for each vendor at intake. Owners should accept risk and own renewals. A third pitfall is setting monitoring alerts too aggressively without routing or context. Calibrate thresholds, add context to alerts, and send them to the vendor owner with clear next steps.
Finally, do not wait until renewal season to clean up data. Run a monthly report of vendors with missing owners, expired documents, or inactive monitoring. The goal is a steady rhythm, not a year end scramble.
FAQ
What is vendor risk management automation?
It is the use of workflow, rules, and integrations to move vendor intake, assessments, approvals, monitoring, and renewals through a consistent path. The result is faster onboarding and better audit trails. It includes vendor security questionnaire automation, approval routing, continuous vendor monitoring, and contract renewal automation.
Which questionnaire standard should we use?
Use SIG Lite for low risk, SIG Core for moderate to high, and SIG Detail for the deepest reviews. For cloud services, consider CAIQ. Both SIG and CAIQ are widely accepted and enable repeatable mapping to frameworks. Learn about SIG here and CAIQ here.
Why add continuous monitoring if we already do annual reviews?
Because risk changes between reviews. Continuous monitoring reduces reliance on point in time assessments and lets you react when a vendors risk posture changes. See Bitsight guidance here.
Can AI really answer questionnaires for us?
AI and knowledge base systems can answer recurring questions by pulling from approved content, then route items that need human judgment. OneTrust and Whistic both offer this approach. See OneTrust here and Whistic here.
How does this help with audits?
Automation produces a consistent record of who approved what, when evidence was reviewed, and how exceptions were handled. CLM systems add contract history and renewal decisions. ContractWorks explains renewal tracking and audit trails here.
What if we already use a procurement suite?
Great. Keep it. We connect intake and approvals to that system, then add questionnaire routing, monitoring, and CLM integrations as needed. The point is to remove manual steps in the lifecycle you already have.
Your next step
If you are ready to shorten cycle time and reduce manual work without increasing risk, we are ready to help. Start with a short call where we map your intake through renewal process and identify three to five high value automations. We can then deliver a proof of value that your team can try with real vendors. Learn more about custom automation and workflows and our automation playbooks and guides. If you prefer to move straight to planning, request a free consultation on automation.
We are also building a downloadable checklist that maps SIG and CAIQ items to automation actions. If you want early access, contact us and we will share the draft while we finalize the public release. In the meantime, if you want us to design a vendor risk automation services plan for your organization, reach out and we will schedule a 30 minute discovery call.
Book a 30 minute discovery call
This playbook showed how vendor risk management automation brings order to intake, standardizes assessments with SIG and CAIQ, uses AI to answer repetitive questions, routes approvals without delays, adds continuous vendor monitoring to catch changes, and keeps renewals and offboarding on schedule with CLM. When these pieces connect you get faster purchasing, better visibility, and a calmer team.